Threat Detection and Secure Logging for the IBM i
Threat Detection and Secure Logging for the IBM i
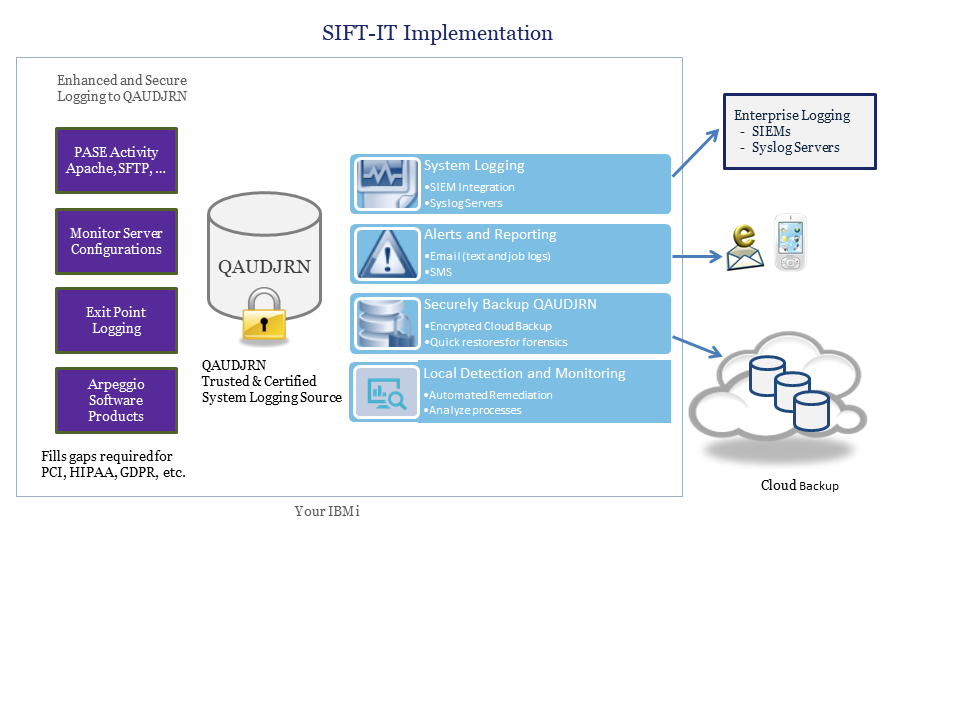
SIFT-IT is an enterprise grade security threat detection and secure log management solution for the IBM i that performs real-time monitoring of all types of system and server logs. Unlike legacy products that simply harvest journals and archive them to syslog servers, SIFT-IT can analyze the contents of the logs to filter and manage specific events based on granular details.
Some of the types of events can include invalid logins, logins outside of your network or outside of normal business hours, and changing system values. With SIFT-IT you can also monitor IFS directory activity and processes that use adopted authority and much more.
While other offerings boast about real-time journal harvesting and sending logs to remote servers SIFT-IT goes well beyond that by providing customers the ability to automate remediations in real time through triggering programs when specific events occur. This means you can stop things from continuing immediately rather than waiting for someone to discover it later on a SIEM console or syslog server.
SIFT-IT has unlimited reformatting and integration capabilities to any enterprise SIEM or threat detection software by providing output options for CEF, LEEF, Syslog formats supporting RFC3424 or RFC5424 or even directly outputting to text files for other types of monitoring processes. Customize the payload to remote servers by adding searchable tags which is very necessary to prioritize event correlation on SIEM servers that have tremendous amounts of data.
The backbone of SIFT-IT is its intelligent granular event filtering inside of the agent configurations. The agent configurations allow companies to build specific rules on how to handle a specific event or sets of events in real-time. Ways to address events can include calling processes to disable users, blocking IP addresses and sending high priority alerts including text messages to security personnel. And of course agents also define what SIEM or syslog servers should receive system logs and how to connect to the servers including secure TLS connections.
Since SIFT-IT was designed for high volume environments needing automated remediation Arpeggio created a platform for generating data sets for testing events. The platform includes features for generating and separating event data for testing the handling of specific events. Test cases allow users to extract actual events from QAUDJRN to build localized tests to run through agent configurations prior to implementing into production. This test platform ensures accurate detection and handling of threats rather than implementing into production and tweaking it later. No other IBM i syslog agents provide this type of comprehensive local testing platform.
Consistent with Arpeggio’s standard of securing its applications, SIFT-IT logs its own events in QAUDJRN like editing configs, starting and stopping agents. SIFT-IT tracks before and after snapshots of modified agent configurations too.
SIFT-IT has successfully integrated to many different SIEM systems and syslog servers including:
- IBM QRADAR
- Cisco Splunk
- Sumo Logic
- Alert Logic
- LogLogic
- ArcSight
- SolarWinds
SIFT-IT is proven in many industries including financial, banking, insurance, healthcare, retail, transportation and manufacturing. Some of our clients process as much as 10,000 security events per second for secure logging to multiple SIEM applications simultaneously.
If you need a high volume, sophisticated security detection solution for the IBM i, SIFT-IT is right for you! See for yourself and download a trial of SIFT-IT.